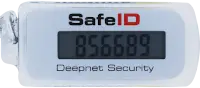
Deepnet Pre-programmed Security Hardware Tokens
Pre-programmed tokens are ready to be used out of box. Then can be easily and quickly deployed to users by the system administrator without user’s involvement. That is why it is very popular, particularly in a large user base.
Pre-programmed tokens are supported by many popular MFA systems, such as Azure MFA (with Azure AD P1 or P2), OKTA, Duo etc
How they work
Every one-time password (OTP) token generates different and unique numbers, that is because every token is programmed with a unique piece of code called secret or seed. Pre-programmed tokens are programmed at factory, and cannot be re-programmed. Pre-programmed tokens come with a token file that contains the secrets of all of tokens. The customer’s system administrator will upload the token file onto their service account, such as Azure AD account, and assign tokens to their users. Once a token is assigned to a user, it is ready to be used by the user without further actions.
Programmable Tokens
Programmable OTP tokens allow customers and users to program their tokens with their own seed or secret data. Basically, programmable tokens are just like the OTP mobile app such as Google Authenticaor or Microsoft Authenticator, and they are often used to replace those OTP mobile apps.
Programmable OTP tokens can be used in any system that supports Google Authenticatior or Microsoft Authenticator, such as Office 365 and Google G-Suite etc.
How they work
Every one-time password (OTP) token generates different and unique numbers, that is because every token contains a unique piece of code called secret or seed. Most cloud services such as Office 365 generate the user’s secret and provides it as a QR code. Using a programming tool, the user’s secret can be programmed into a programmable hardware token by scanning the QR code. This process is exactly the same as that the user’s secret is installed into the Microsoft Authenticator or Google Authenticator app.
You can program hardware tokens using a Windows PC or laptop with a NFC Smart Card Reader, Android phone with NFC function, or iPhone with NFC function.
Once a hardware token is programmed, it works on its own. It doesn’t connect to your phone or the internet in order to generate one-time passwords.
Deepnet Security’s NFC Reader
The Deepnet Security’s NFC Reader is a PC-linked contactless smart card reader/writer developed based on 13.56 MHz contactless (RFID) technology. Compliant with the ISO/IEC 18092 standard for Near Field Communication (NFC), it supports not only MIFARE and ISO 14443 A and B cards, but also all four types of NFC tags.
How they work
The NFC reader supports both CCID and PC/SC programming interface. Thus, it is a plug-and-play USB device allowing interoperability with different devices and applications. With an access speed of up to 424 kbps and a full USB speed of up to 12 Mbps, the NFC reader can also read and write more quickly and efficiently. The proximity operating distance of the reader is up to 5 cm, depending on the type of contactless tag in use.
FIDO Security Keys
Based on free and open standards from the FIDO Alliance, FIDO Authentication replaces password-only logins with a specialized USB, NFC or BLE device – a FIDO key. FIDO enables users to securely access desktop and laptop machines, web and cloud applications with one single security device, instantly and without driver software.
How they work
In other words, SafeKey security device can be used as a FIDO key and a OTP token. SafeKey contains no battery and requires no driver to use. It supports Windows, MacOS, Android, iOS. It can used as a logon device for Windows PC, Mac workstation, Web applications and Cloud services.